Cyber Security matters - #7 Malicious URLs
Posted on behalf of: Better Campus
Last updated: Wednesday, 28 August 2024

As part of our Cyber Security awareness campaign, we’re covering a new topic each month to help boost your knowledge and keep you and the University safe and secure.
Phishing is when a cybercriminal designs an email, text message or website to look like it has come from a legitimate company or organisation. Their goal is to lure individuals into providing sensitive data such as personal information, bank or credit details, and passwords, or to infect your devices with malware.
This month we are focusing on identifying malicious URLs (Uniform Resource Locator) which are links found in phishing messages that lead to a website that it is some way dangerous to you or your device.
What to look out for in a link
The devil is in the detail. Before clicking on any URL link contained within an email, there are key details that you can look out for to help identify potentially dangerous links:
- Spelling ‘errors’ - additional, missing or changed letters in well-known domains that try to imitate a brand’s domain
- Shortened links that condense a longer link to conceal the true destination
- Punctation can be added to a brand’s official domain to disguise a malicious link
- Number-based URLs are sometimes used, as legitimate websites usually have descriptive word-based domain names
- When looking at website addresses, sometimes extra words are added before the main site name - these extra words might include the brand’s name, making it hard to tell if the site is real or not
- HTTPS is a part of a web link that usually indicates the connection is secure, meaning information sent to and from the site is safe. However, cybercriminals can fake this to trick people.
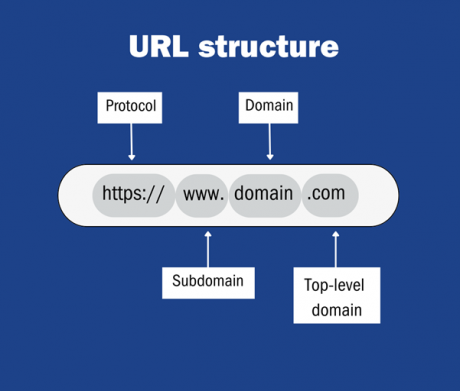
The way a website address (URL) is put together can reveal important details. A URL structure should be:
What will happen if I click on a malicious link?
There’s a chance that nothing will happen and that you will immediately see that it’s a suspicious website and leave. But it could also lead to data theft; phishing campaigns are designed to steal credit card information, login details and other personal information. It could also lead to malware being installed on your device, which might encrypt your data, shower you with ads, or steal your passwords.
Real life examples
We have some examples taken from digital and security agencies that highlight the prevalence of URL-based threats.
Security company Proofpoint’s recent threat intelligence data report shows that the average number of daily URL-based threats has increased to over 4.5 million. This is an alarming 119% rise over the past three years.
The report highlighted the speed at which these attacks can cause damage. Research from Proofpoint shows that 1 in 7 clicks on an unsafe link happen in less than 60 seconds after an email’s delivery.
Source: What Is Threat Intelligence? Definition | Proofpoint US
JISC, who provide the UK's national research and education network, reported in 2023 on a major rise in phishing campaigns, with financial-related phishing emails being a common theme. They assisted an organisation who experienced a live phishing campaign affecting over 20 individual user accounts, involving the use of the legitimate social media reference landing page, Linktree, to embed an AiTM (adversary in the middle) fake landing page to bypass email filters.
Source: Jisc Quarterly Threat Report 2023
How to learn more
Each month, we’ll be releasing a matching bitesize training via Proofpoint, our online learning platform. Join us this month for our interactive sea-based cyber adventure game.
Look out for the August update in your inbox on Tuesday 20 August.

